What Makes the Best Cyber Security Services in Dubai Stand Out on the market
What Makes the Best Cyber Security Services in Dubai Stand Out on the market
Blog Article
The Significance of Cyber Protection in Protecting Your Digital Assets
In today's electronic period, the importance of cyber protection in protecting your electronic properties can not be overemphasized. As technology developments, so do the methods of cybercriminals, making robust cyber defenses vital for people and organizations alike. From personal data to important organization information, the threat landscape is large and ever-changing. Carrying out efficient cyber security practices is not simply a suggestion but a necessity to minimize risks and ensure continuity. What strategies can you adopt to stay one action ahead and fortify your digital presence versus these relentless hazards? The solutions could shock you.
Recognizing Cyber Risks
In the swiftly progressing landscape of electronic modern technology, comprehending cyber hazards is paramount for securing electronic properties. The term "cyber threats" includes a large array of malicious activities aimed at jeopardizing the honesty, confidentiality, and availability of info systems.
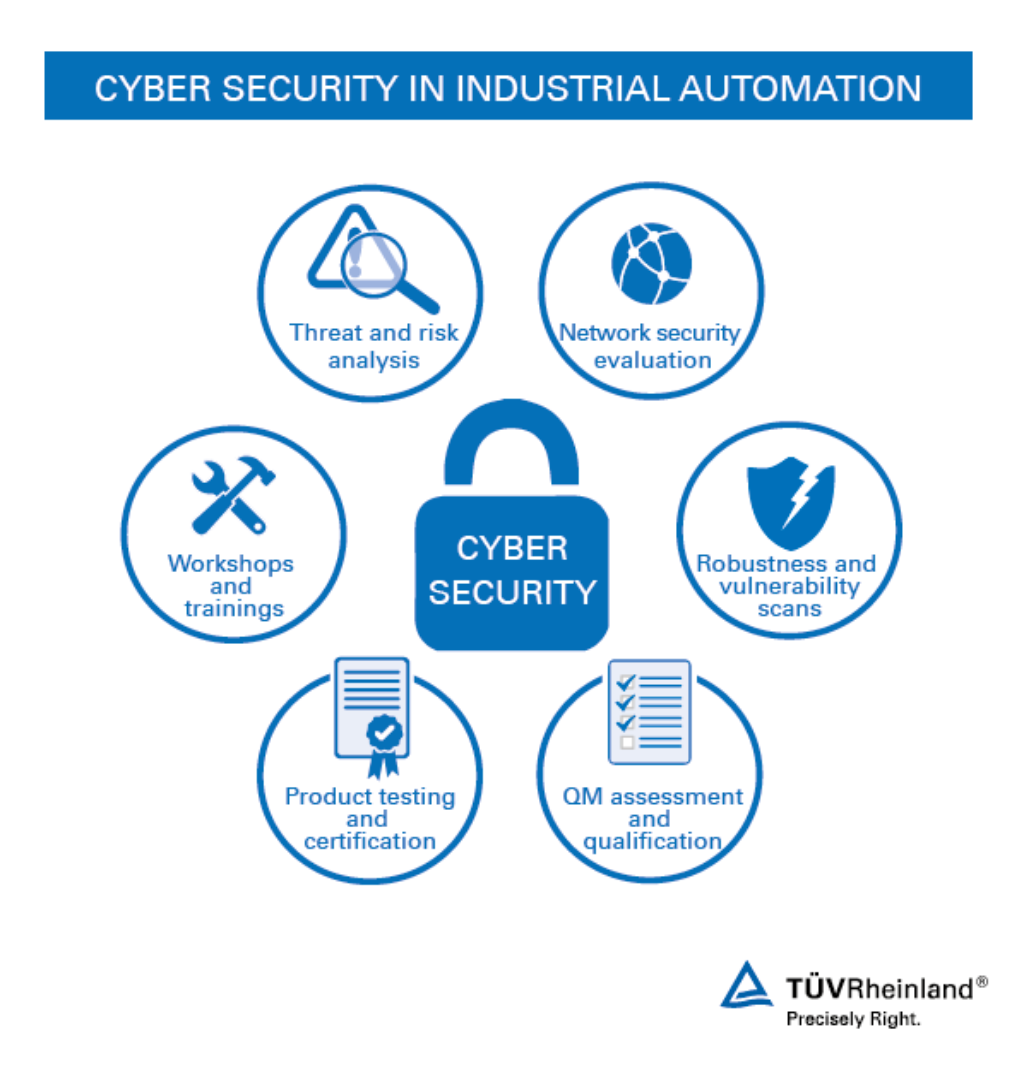
Recognizing the motivations behind these hazards-- be it monetary gain, reconnaissance, or hacktivism-- is vital for creating effective countermeasures. This expertise equips organizations to prepare for potential hazards, tailor their defenses, and eventually shield their important electronic assets from cyber opponents.
Secret Cyber Security Practices
Network security is one more essential element - Best Cyber Security Services in Dubai. This entails the use of firewall softwares and invasion detection systems to keep an eye on and regulate outward bound and incoming network web traffic, properly blocking questionable tasks. Frequently upgrading software and systems is similarly vital, as it patches known vulnerabilities that cybercriminals can manipulate
Information encryption is an important technique that makes sure delicate details is only available to licensed customers. By transforming information into a code, it becomes unreadable without the decryption key, therefore shielding it from unauthorized access during transmission or storage.
Educating workers and individuals regarding cyber safety finest techniques is likewise crucial - Best Cyber Security Services in Dubai. Normal training sessions can elevate awareness regarding typical risks like phishing and social engineering, equipping people to acknowledge and avoid potential dangers. By integrating these key practices, organizations can build a resistant protection versus the ever-changing landscape of cyber hazards
Protecting Personal Information
Guarding individual data has become a necessary in today's electronic age, where the volume of information exchanged online is surprising. This data incorporates every little thing from social protection numbers to individual health records, and its defense is vital for preserving privacy and security. People need to be attentive in guaranteeing that their personal details is not jeopardized, as breaches can lead to identity burglary, monetary loss, and reputational damages.
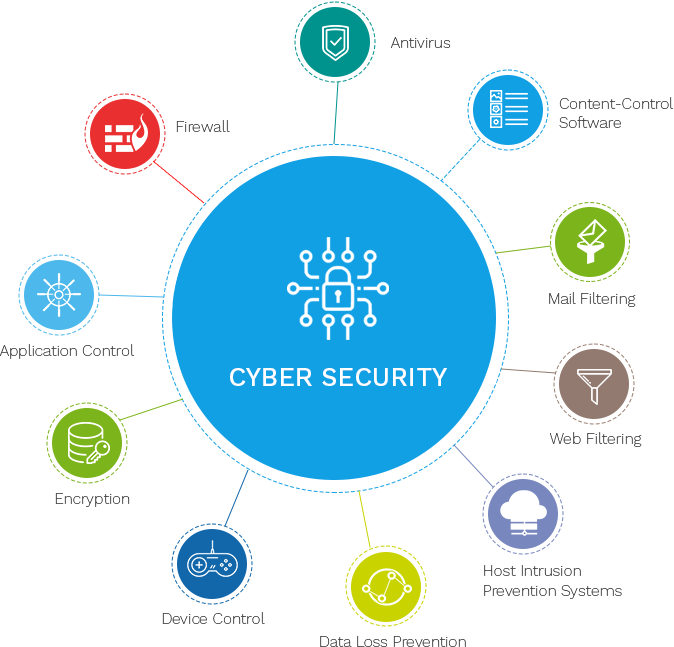
Understanding of phishing attempts is crucial, as cybercriminals frequently make use of misleading emails and websites to swipe personal information. People ought to verify the resource of unwanted interactions and prevent clicking suspicious web links. Finally, securing individual gadgets with anti-virus software application and firewalls can better fortify defenses against unapproved access and possible dangers.
Shielding Company Details
While shielding personal data continues to be a priority for individuals, organizations deal with the wider challenge of securing substantial quantities Homepage of delicate details that drive their procedures. Carrying out durable cyber protection actions is not simply an alternative however an essential need for organizations of all sizes.
To properly secure company details, a multi-layered security technique is essential. This need to encompass firewall programs, file encryption, intrusion detection systems, and regular safety audits.
Moreover, services should establish and routinely update case reaction strategies. Being planned for potential breaches makes certain quick activity to minimize damage. By purchasing detailed cyber security techniques, services not just protect their assets however likewise enhance count on with their clients and companions, ultimately securing their market setting and future growth.
Future Patterns in Cyber Safety
As the electronic landscape swiftly evolves, future trends in cyber safety and security are positioned to redefine how companies safeguard their digital possessions. One popular pattern is the increase of expert system (AI) and maker discovering (ML) in danger discovery and feedback. These modern technologies make it possible for much faster recognition of abnormalities and prospective risks, enabling much more effective and automated responses to cyber cases. Businesses are increasingly adopting AI-driven devices to improve their cyber defense capabilities.
As remote job becomes more prevalent, standard perimeter-based safety and security versions are proving insufficient. The zero-trust strategy needs continual verification of gadgets and individuals, also within the network, thereby lessening possible attack vectors.
Furthermore, quantum computing is becoming both a hazard and an opportunity. While it assures exceptional handling power, it postures risks to current file encryption techniques. Organizations has to plan for post-quantum cryptography to safeguard their data.
Lastly, privacy-enhancing modern technologies are gaining momentum. With enhancing regulative focus on information security, services are spending in devices that make certain conformity while keeping functional performance. These future fads emphasize the vibrant and ever-evolving nature of cyber protection.
Verdict
In a significantly interconnected electronic landscape, the execution of durable cyber protection procedures is necessary to protect digital assets from evolving hazards such as ransomware, malware, check these guys out and phishing. Utilizing methods like strong passwords, multi-factor verification, and normal software application updates improves the protection of sensitive Discover More details, mitigating threats of identification theft and financial loss. Structure understanding and adopting advanced protection methods foster durability and trust, making certain the integrity and connection of both personal and service electronic operations when faced with future cyber obstacles.
In today's digital age, the value of cyber security in securing your electronic properties can not be overstated.Executing effective cyber protection practices is critical in safeguarding electronic possessions against advancing threats.As the digital landscape swiftly advances, future trends in cyber safety are positioned to redefine just how businesses protect their electronic possessions.In an increasingly interconnected electronic landscape, the implementation of robust cyber protection steps is crucial to protect electronic assets from progressing hazards such as ransomware, malware, and phishing. Building understanding and embracing innovative security methods foster strength and trust, making sure the honesty and continuity of both personal and company electronic procedures in the face of future cyber obstacles.
Report this page